As blockchain adoption grows, so do risks like frontrunning attacks, token scams, and cross-chain vulnerabilities. Blockchain security protocols are crucial in this regard, ensuring that every step of a transaction — from initiation to confirmation — is protected. Understanding end-to-end transaction security is key for users and developers to avoid losses and ensure safe, uninterrupted network interactions. This article explores the top protocols ensuring secure blockchain transactions in 2024.
In this guide:
- Top 5 blockchain protocols
- What is end-to-end transaction security?
- Is it enough to secure transactions with blockchain security protocols?
- Frequently asked questions
Top 5 blockchain protocols
In brief, some of the top blockchain security protocols in 2024 include:
- Omnia Protocol – Frontrunning protection with private mempools
- LayerZero – Private relayers for secure cross-chain communication
- Chainlink CCIP – Multi-layer validation for token transfers
- Wormhole – Guardian nodes for cross-chain transaction safety
- Cosmos Hub (IBC Protocol) – Secure asset transfers with Tendermint consensus
Let’s examine each blockchain security protocol in detail.
1. Omnia Protocol: Best for preventing exploits
Omnia Protocol ensures that blockchain users and developers enjoy secure and private access to networks without fear of frontrunning, token scams, or malicious interactions.
By safeguarding transaction data from initiation to completion, Omnia delivers end-to-end security and keeps every blockchain operation confidential.
Users: Omnia protocol
How it works?
Omnia acts like a guarded tunnel for blockchain transactions. When a user interacts with a blockchain through Omnia’s private RPC endpoints, the data is hidden from public view, protecting it from attackers. These private mempools prevent bots from frontrunning trades or intercepting sensitive information.
In addition, Omnia detects honeypots — scam tokens designed to trap users — by analyzing smart contracts and transaction data in real-time.
Omnia is also blockchain-agnostic and supports continuous transaction monitoring and multiple networks, ensuring the broadest possible security coverage.
Pros
- Prevents frontrunning attacks: Private RPCs keep transactions hidden from bots.
- Blocks scam tokens: Honeypot detection stops users from interacting with fraudulent tokens.
- Multi-chain support: Works across several blockchains, ensuring flexibility.
Cons
- Technical setup: Users may need time to understand private RPCs and honeypot protections.
- Node dependency: Requires consistent participation from nodes for uninterrupted access
2. LayerZero: Best for secure cross-chain transactions
LayerZero ensures that transactions between different blockchains are completed safely and without interruption. Cross-chain transactions often introduce new risks, such as frontrunning and incomplete transfers, but LayerZero eliminates these vulnerabilities by securing every part of the transaction — from initiation on one blockchain to confirmation on another.
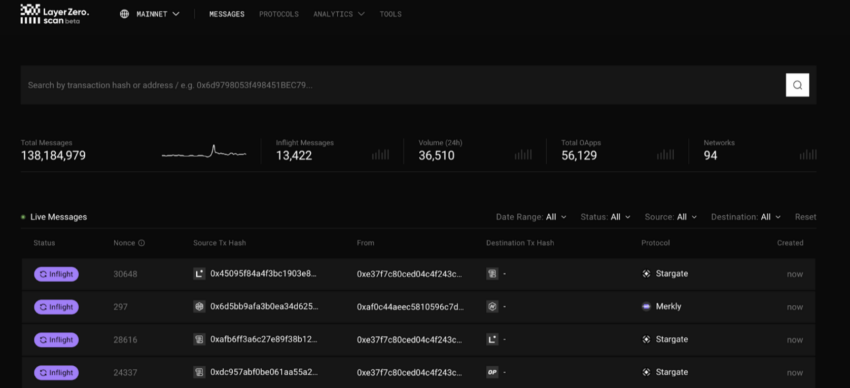
Interface: Layer Zero
How it works?
LayerZero maintains speed and security by using a combination of ultra-light nodes (ULNs), oracles, and relayers. Think of it like sending a package through a trusted courier network, where the couriers (relayers) and validators (oracles) confirm that the package reaches its destination intact without interference from outsiders.
Ultra-light nodes (ULNs) validate transactions without requiring the entire blockchain’s data, which keeps the network agile while maintaining security.
Relayers transmit the transaction data between blockchains while keeping it hidden from public exposure, ensuring that no one can intercept the data or manipulate the transaction.
Oracles independently verify transactions at both the source and destination chains, maintaining data integrity even during cross-chain swaps.
In terms of end-to-end transaction security maintenance, the private relayers protect transaction data from being manipulated or intercepted, whereas the ULNs ensure secure validation.
Plus, each network component functions independently, consequently reducing the risk of system-wide vulnerabilities. This is all thanks to the resilient modular design.
Pros
- Frontrunning mitigation: Private relayers keep transactions out of public mempools.
- Fast cross-chain execution: Ultra-light nodes speed up transactions without compromising security.
- Reliable verification: Oracles ensure every transaction is correctly validated, protecting user assets.
Cons
- Complex setup: Users may initially find the architecture involving relayers and oracles difficult to grasp.
- Dependency on validators: While decentralized, LayerZero’s operation relies on validators functioning properly.
3. Chainlink CCIP: Best for securing token transfers
Chainlink’s Cross-Chain Interoperability Protocol (CCIP) offers a reliable way to transfer tokens between blockchains while preventing transfer errors or manipulation. By verifying transactions at several points, CCIP ensures every transfer is secure from start to finish, making it an essential tool for safe cross-chain operations.
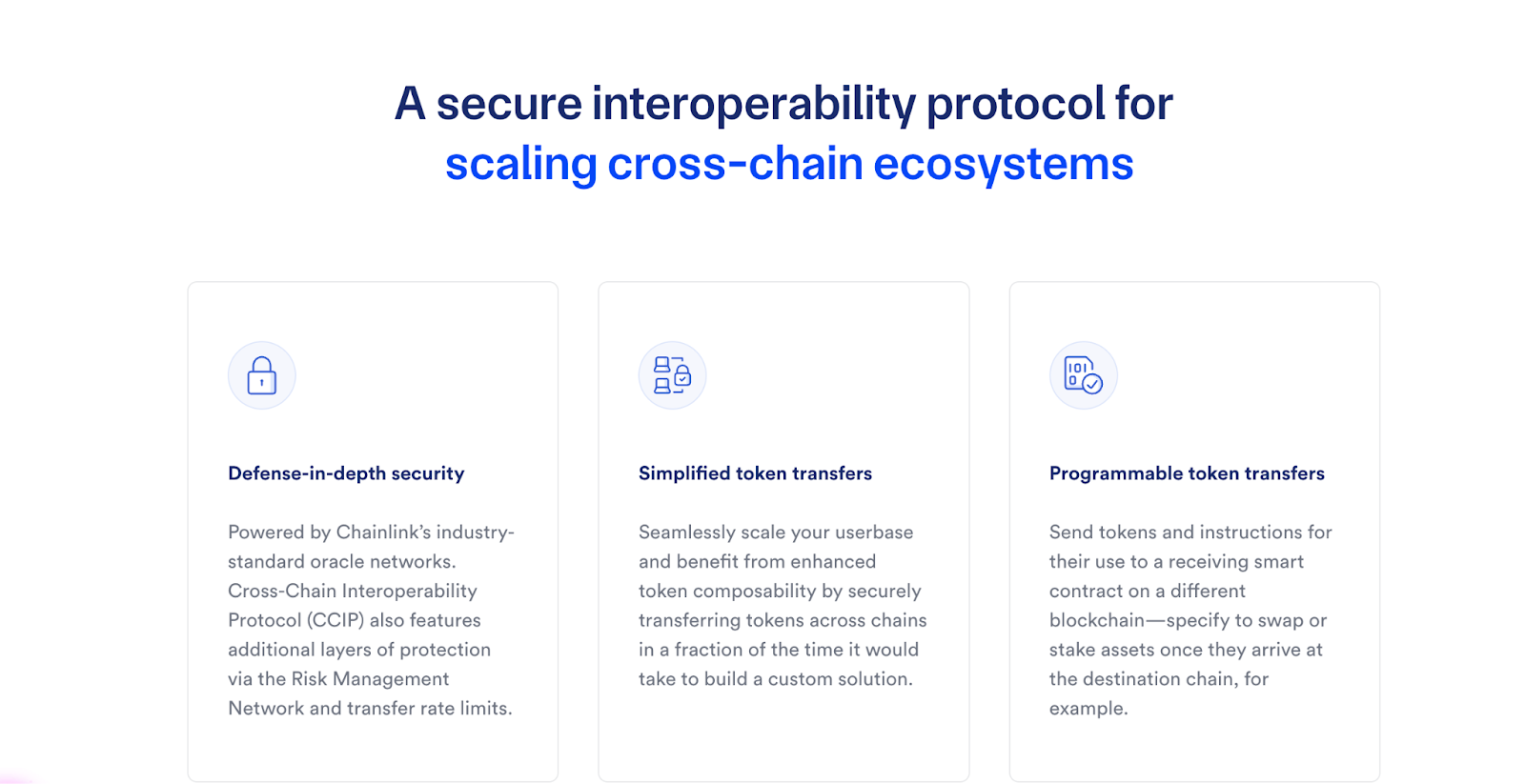
Chainlink protocol: Chainlink
How it works?
CCIP acts like a checkpoint system for blockchain transactions. When sending tokens between networks, oracles and validators work together to confirm each step of the process.
Imagine mailing a package where each post office stamps it along the route —this ensures the package hasn’t been tampered with before it reaches its destination.
Chainlink CCIP uses multi-point validation, private communication channels, and flexible token handling for safer transfers and error prevention.
Pros
- Frontrunning protection: Keeps transactions out of public view to prevent interference.
- Secure token transfers: Validates transactions at multiple points to prevent mistakes or loss.
- Cross-chain flexibility: Supports many networks for seamless movement of assets.
Cons
- Learning curve: Users may need time to understand programmable transfers.
- Reliance on Oracles: The process depends on validators and oracles working properly.
4. Wormhole: Best with guardian verification
Wormhole ensures that assets and data can move securely between multiple blockchains, reducing the risks involved in cross-chain transactions.
With its guardian node system, Wormhole ensures each transaction is verified independently, blocking unauthorized or tampered transfers and ensuring the transaction remains secure from start to finish.
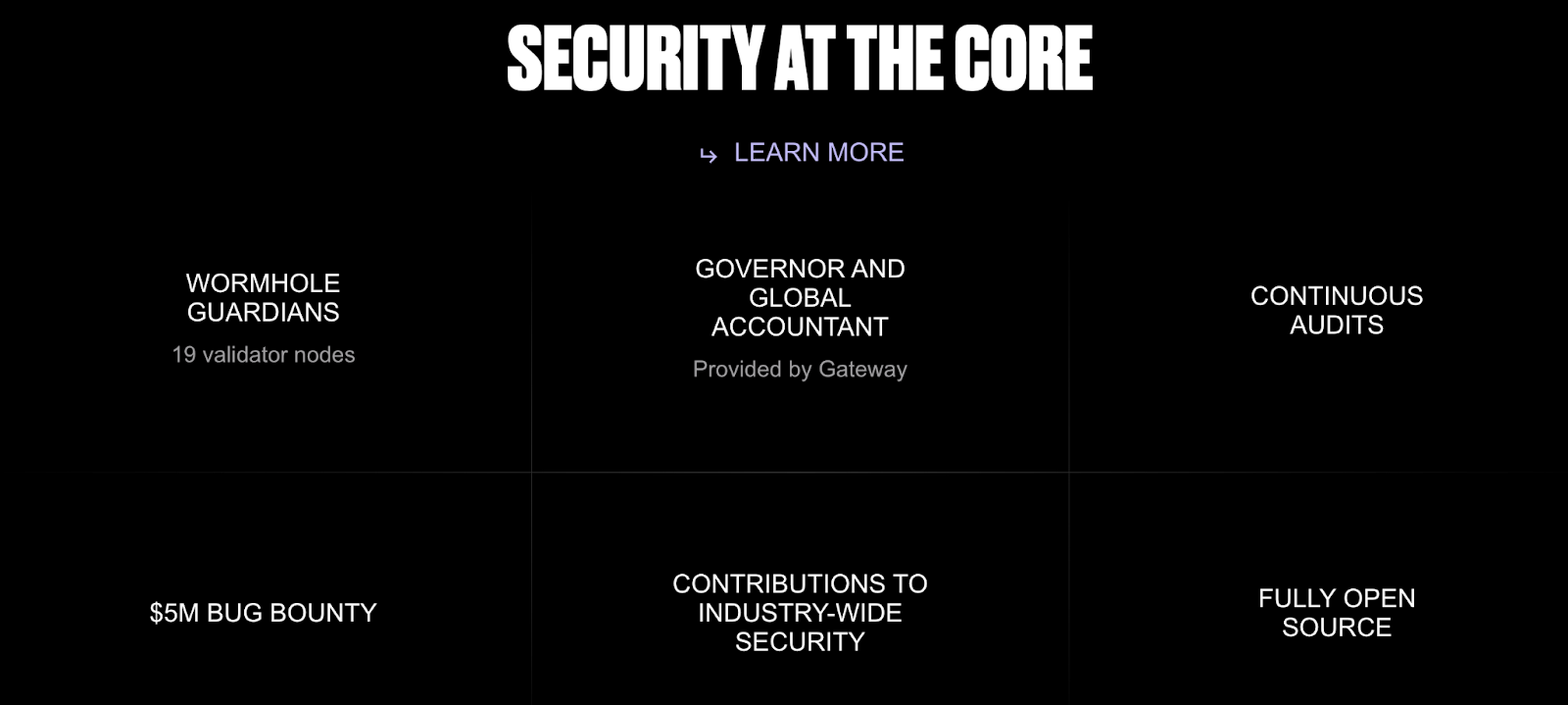
Wormhole interface: Wormhole
How it works?
Wormhole functions as a bridge between blockchains, facilitating asset transfers with the help of guardian nodes. Think of the guardian nodes as checkpoints on a highway — every time a vehicle (transaction) passes through, it is inspected to ensure it meets all safety standards.
When a transaction is initiated on one blockchain, the guardian nodes validate it before it reaches the destination blockchain. If they detect any discrepancies, the transaction is rejected, ensuring that only legitimate transfers are processed. This ensures that end-to-end transaction security is maintained even when assets or data are transferred across different networks.
Wormhole is one of the few blockchain security protocols that rely on a decentralized bridge design. Plus, there is access to asset recovery tools.
Pros
- Guardian verification: Protects transfers by checking every step independently.
- Decentralized security: Reduces reliance on a single validator, preventing system-wide vulnerabilities.
- Recovery mechanisms: Provides tools for handling failed or stuck transactions.
Cons
- Bridge vulnerability risks: Like other cross-chain bridges, Wormhole is exposed to evolving attack methods.
- Complex setup: Users may need time to understand the guardian node system.
Cosmos Hub: Best for secure asset transfers using the IBC protocol
The Cosmos Hub enables secure cross-chain transactions using its Inter-Blockchain Communication (IBC) Protocol. It ensures that assets and data move safely between connected networks, maintaining integrity throughout the transaction. Cosmos reduces the risk of incomplete or manipulated transfers, ensuring every step — from sending to receiving — is handled securely.
Cosmos Hub: Cosmos
How it works?
The IBC protocol functions like a secure delivery network. When a user sends tokens from one blockchain to another, IBC ensures that both chains validate the transfer before it completes. Think of it as a two-way handshake: the sending chain locks the tokens, and the receiving chain issues an equivalent amount only when the first step is confirmed. If any problem arises during the process, the transaction is halted, protecting the assets from loss.
IBC also uses Tendermint consensus to maintain trust and consistency across blockchains, ensuring that transactions are correctly validated without delays or manipulation.
Pros
- Prevents asset loss: Two-way validation ensures that assets are never lost in transit.
- Fast and consistent: Tendermint consensus provides quick validation without compromising security.
- Resilient to downtime: IBC can handle network interruptions and secure assets until recovery.
Cons
- Network coordination: Requires coordination between multiple blockchains, which can introduce complexity.
- Limited adoption: Some networks are still integrating IBC, limiting its current use cases.
What is end-to-end transaction security?
End-to-end transaction security ensures that every transaction, from initiation to completion, is protected from risks like manipulation, frontrunning, or incomplete execution.
This concept guarantees that no unauthorized entity can interfere with or alter a transaction, providing users with complete confidence in their blockchain activities.
Without proper end-to-end security, blockchain transactions risk exposure to frontrunning, phishing, or incomplete transfers.
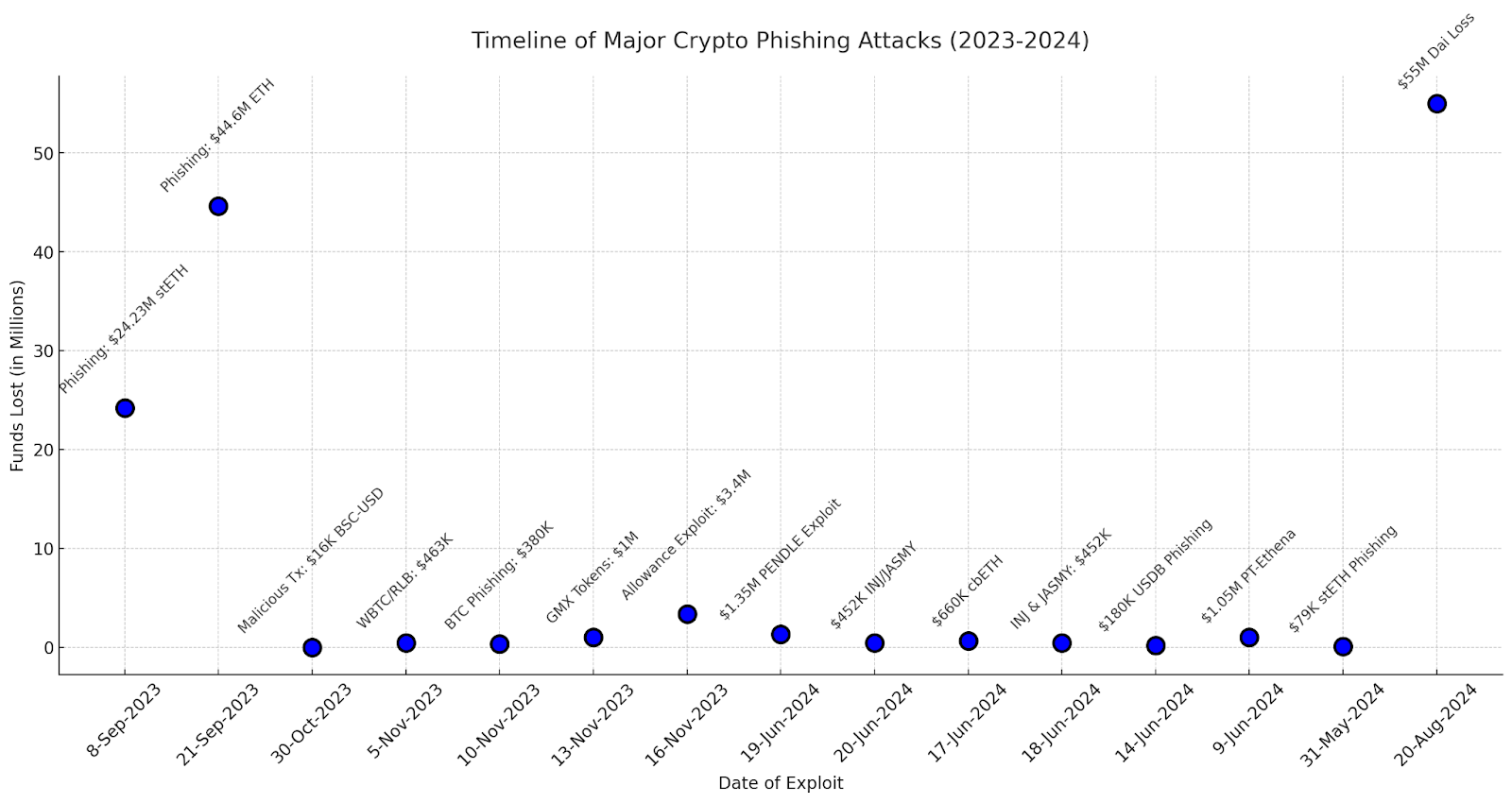
Timeline of major phishing events: BIC
Blockchain security protocols ensure users’ funds remain safe, interactions with smart contracts are trustworthy, and data is not leaked or manipulated along the way.
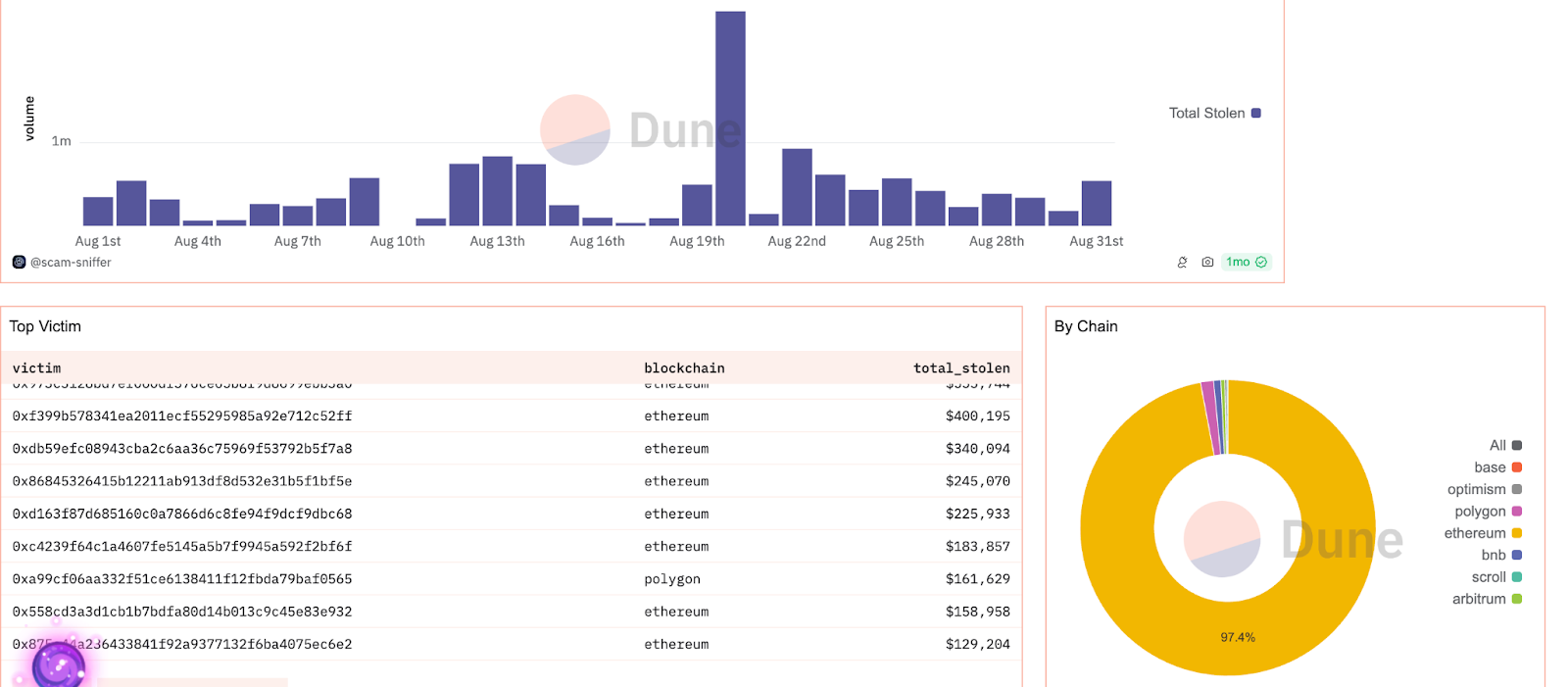
Recent phishing trends: Dune
Is it enough to secure transactions with blockchain security protocols?
Blockchain security protocols are a critical step toward safe transactions. However, they may not be enough on their own. While these protocols provide end-to-end security by preventing manipulation and verifying data, evolving threats require continuous upgrades.
A multi-layered approach — including user awareness, audits, and additional safeguards — ensures stronger security and trust across decentralized networks.